Using Hardware Security Keys in Gyroscope October 8, 2021
Hardware security keys using FIDO2 or FIDO U2F are now supported in Gyroscope v18.7. This means that more secure and convenient authentication options such as USB, NFC and Bluetooth keys, as well as fingerprint sensors through mobile devices' screen lock are all supported.
The fingerprint icon on the login screen allows a hardware secured user to sign in without a password. The username has to be entered first before clicking the fingerprint icon:
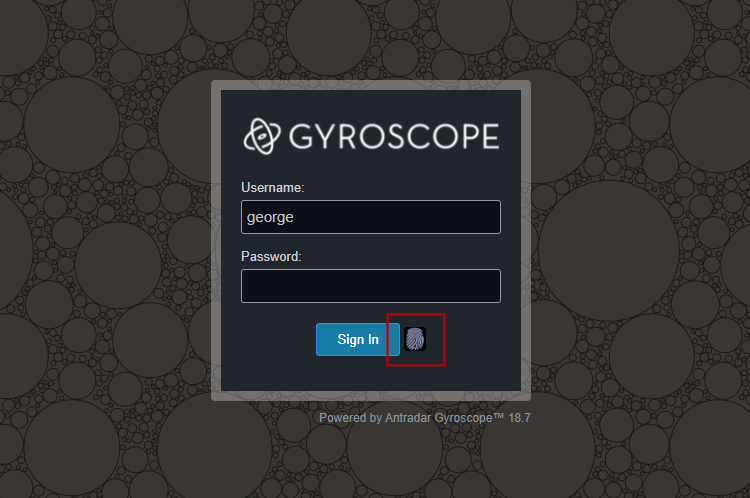
Upon successful login, the username will be remembered for the next session. This simplifies repeated sign-on.
If the user has no enrolled devices, the fingerprint icon does nothing, which is to be expected.
The setup of a security key is left to individual users. This means that an admin user cannot configure keys on behalf of other users. Resetting another user's password, however, will clear all the security key and additional 2FA requirements. This helps reviving a user that's "locked out" of the system.
To set up a security key, go to Account Settings by clicking on the user icon on the top right corner of the Gyroscope interface. Then check the box that says "enable hardware security keys and screen lock":
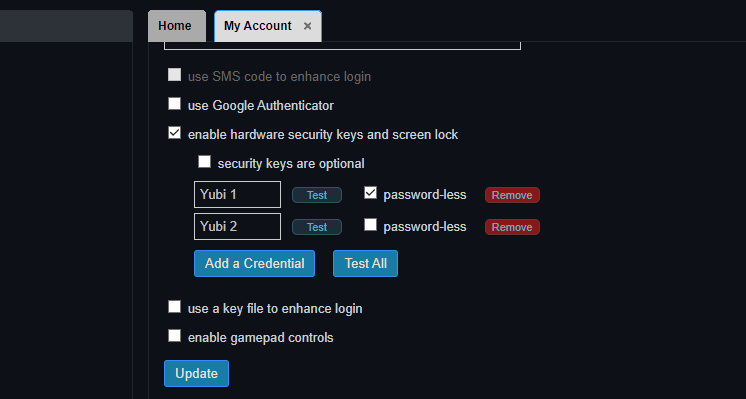
You can enroll multiple keys and test the keys separately or at the same time. The "Test All" button is useful for identifying which device is picked as a primary authentication method by the system. In fact, one can plug in multiple keys and see which profile matches:

You will be asked to touch the key first before going through the typical key registration steps.
In a browser that supports FIDO2, you will be asked to set up a PIN during the first time of using a security key. The PIN is then required before further verification:
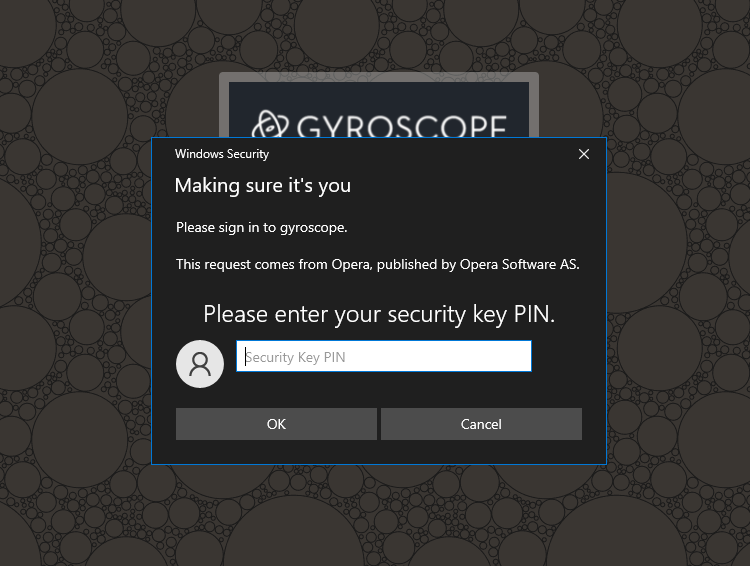
Afterward, you will be prompted to touch the key:
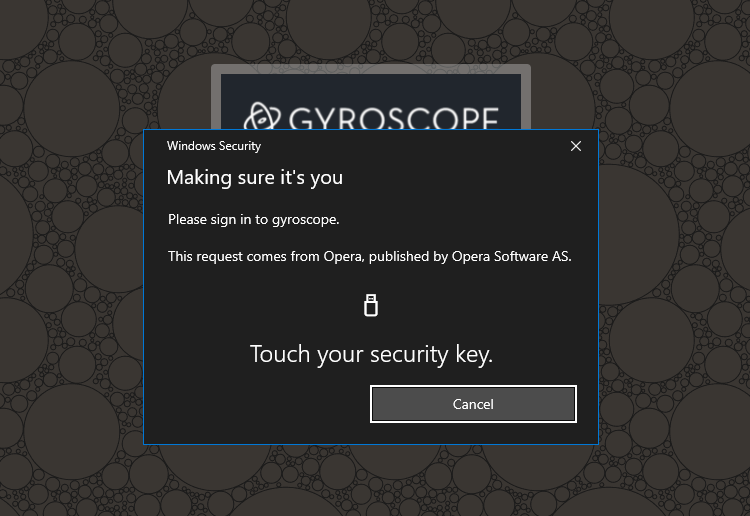
On a mobile device, you might be presented additional options:
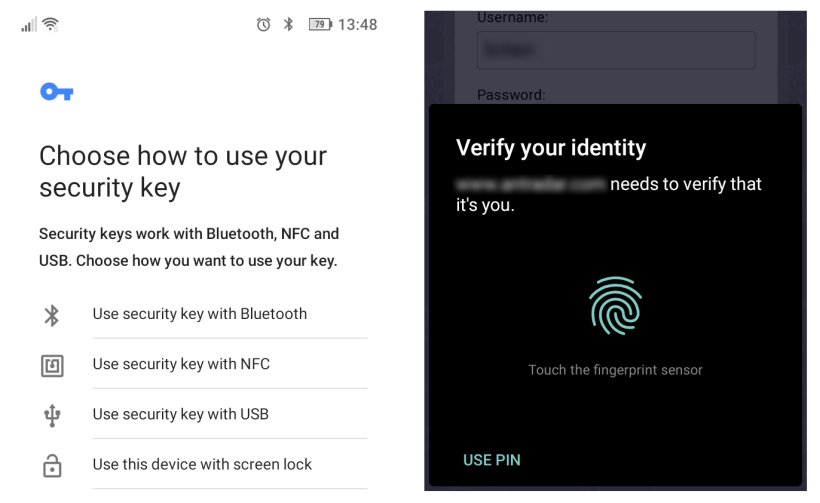
If a finger print is enrolled in the mobile device, it is then supported by the screen lock method. A NFC-enabled security key can also be tapped against the back of the device without selecting the "use security key with NFC" option first.
Convenience vs. Security
Although the flow of adding a physical authentication method is the same for a FIDO2 key, a FIDO/U2F key and a screen lock, the end results might be either convenience or added security. There is unfortunately a tradeoff. Luckily, Gyroscope allows flexible configuration of keys, so that it's up to the user to deploy suitable strategies.
FIDO2 and FIDO/U2F are interfaces that may be supported by the same hardware key. The Universal 2nd Factor (U2F) is intended as an added security rather than replacing passwords. One can argue that a stolen key should not be sufficient to gain access to a critical system. FIDO2 was created to require an additional PIN. The difference in hardware interfaces translates to one extra step in the user interface: can a key be simply tapped to log in, or an extra PIN must be entered first?
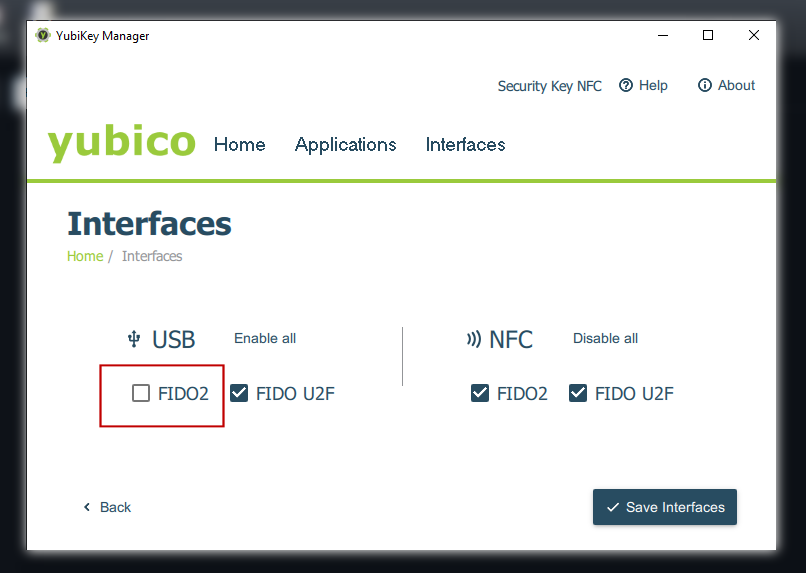
There is one more difference. When a FIDO2 key is configured to run in U2F-only mode, the said key cannot be enrolled in Gyroscope. You will see the following error:
"user must be present and verified"
The same error is given when enrolling a key through an NFC touch. This is by design.
To add an NFC key to an account, use a laptop to enroll the key first. Similarly, a FIDO2 key can be enrolled before switching it to U2F-only mode:
Choices Choices Choices
As said earlier, Gyroscope allows very flexible security policy settings. Not all keys are the same. We can have one key that's PIN protected, and another for expediency. The combination of "security keys are optional" on the account level, and "password-less" on the key level allows the following scenarios:
- Both password and a security key are required
- Either a password or a key can log in
- A password, or a "password-less" key is required
- A key is required, password ignored
Mixing with Other Methods
When additional 2FA methods such as SMS verification or Google authenticator code are enabled, they will be gathered prior to touching the security key. Not sure why anyone would want this configuration but the options are there. After all, someone will do anything to get rid of a password!

